Support your customers, employees and Contact Center agents with Conversational and Generative AI.
Voiceweb enelaitm platform utilizes artificial intelligence (AI), Machine Learning and Natural Language Understanding (NLU) to complete the users’ requests, answer their questions or to suggest the best responses to your agents.
Support your customers, employees and Contact Center agents with Conversational and Generative AI.

AI Virtual Assistants (chatbots)
Conversational IVR

Agent Assist
Voice Biometrics
Speech Recognition

Generative AI

AI Virtual Assistants (chatbots)
with text and/or voice entry for highest self-service rates (typically 88% - 95%).

Conversational IVR
for high IVR self-service (>55%), reduced OPEX and correct routing of all inbound calls.

Agent Assist
with Generative AI (GPT models) for suggesting the best-possible responses to contact center agents during their calls and chats.

Voice Biometrics
for accurate and fast authentication of the users during Agent calls, or in IVR self-service or in chatbots: with only 3 seconds of speech and >92% completion.

Speech Recognition
for IVR calls, chatbots, agent calls (transcription for analytics) and any audio transcription requirement of a contact center or an Enterprise with accuracy up to 95% (5% WER).

Generative AI
Utilizing GPT Large Language Models for greatly improved Customer Experience in chatbots and powerful Agent Assist. With emphasis on personal data protection (PII) and data privacy.
Businesses have been adopting enelaitm AI-powered platform to:
answer frequent questions of consumers (FAQs)
automate Customer Service tasks (self-service)
provide assistance to their Agents while discussing with customers
gather information from consumers e.g. for KYC, lead generation or lead qualification
sell / upsell products and services
enhance the consumers’ shopping experiences
deliver personalized offers & notifications to customers
deliver content and VAS to consumers
enable users to book appointments
provide HR information and documents to employees
provide IT Helpdesk support
generate Contact Center Analytics and Predictive Analytics


Highest Business Results and KPIs
ensuring that all business goals will be fulfilled – and even exceeded.
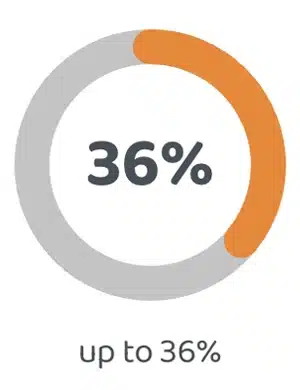
OPEX
Savings
36%
up to 36%
reduction in contact center operating costs
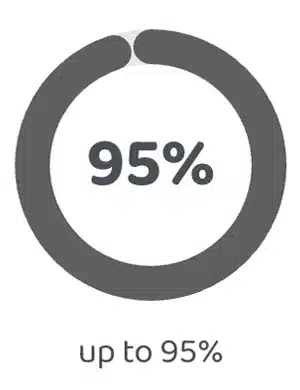
Chatbot
Self-Service
95%
up to 95%
from 88% to 95%
self-service
Speech IVR
Self-Service
58%
up to 58%
from 50% to 58%
self-service
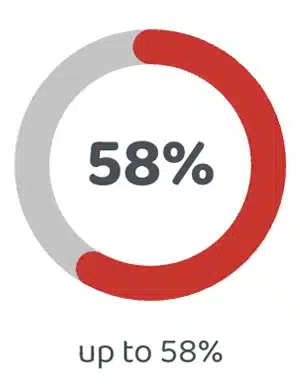
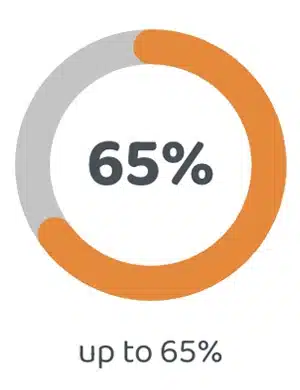
Customer Satisfaction
65%
up to 65%
from +60% to +65% NPS and 8.0 to 8.5 CSAT
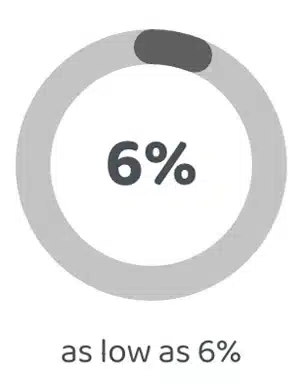
Speech Recognition
6%
as low as 6%
from 6% to 9% WER
(Word Error Rate)
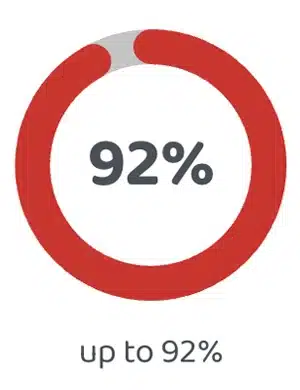
Voice
Biometrics
92%
up to 92%
of authentications completed in IVR and Agent calls within 3 seconds
Highest Business Results and KPIs
ensuring that all business goals will be fulfilled – and even exceeded.
OPEX
Savings
Chatbot
Self-Service
Speech IVR
Self-Service
Customer Satisfaction
Speech
Recognition
Voice
Biometrics
Millions of conversations being successfully
completed every month!
Over 380 million consumers have had their requests successfully serviced by an automated Virtual Assistant created with enelaitm platform. The insights and feedback collected from each deployment are fed back into enelaitm as new functionalities & capabilities.
Pay only for results!
Clear & concise pricing model ensures OPEX
savings and quick ROI for the Enterprise
Do it yourself or collaborate with our specialists
Enelaitm Studio is a No-Code conversation design and collaboration tool packed with features from Voiceweb’s 20+ years of hands-on implementation expertise in developing complex Customer Service projects. Enelaitm Studio offers much more than a typical “bot builder” application allowing designers to easily create any Conversational AI, Voice or Chat-based scenario that may even include complex rules, logic, backend integrations, and more…

Design and implementation services
Voiceweb consultants (and our local partners) work closely with Enterprise client teams -often coming to be thought of more as internal employees rather than external specialists- in order to truly understand each Enterprise's specific business environment and culture, facilitate the free flow of information and ideas, and ultimately deliver a high-quality digital solution that fully meets and exceeds all expectations.
Enterprise-grade platform
Easy integration to the existing infrastructure Enelaitm platform provides pre-built integrations with popular Enterprise software while its versatile architecture allows for almost plug-and-play integration with pre-existing software applications in an Enterprise Contact Center. Meeting Enterprise security and data privacy standards Voiceweb products meet all information security, compliance and payment standards requirements -such as PCI/DSS and GDPR- and have been installed in numerous banks and mobile operators for purchases and financial transactions, after audit and approval from the local Regulators in each country.
Do it yourself or collaborate with our specialists
Enelaitm Studio is a No-Code conversation design and collaboration tool enabling designers to easily create any Conversational AI, Voice or Chat-based scenario that may even include complex rules, logic, integrations to backend applications, and more.
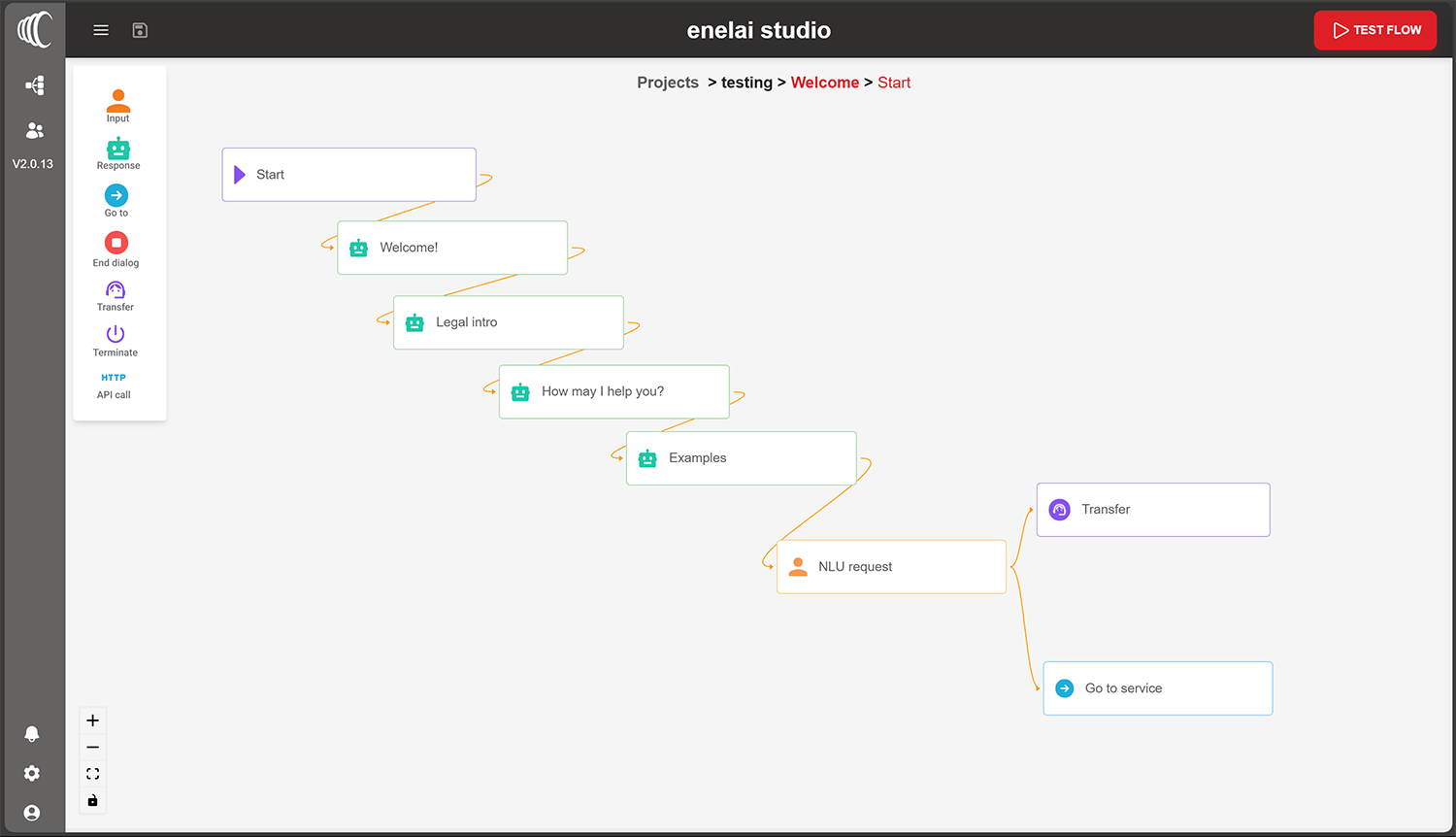

Design and implementation services
Voiceweb consultants (and our local partners) work closely with Enterprise client teams -often coming to be thought of more as internal employees rather than external specialists- in order to deliver a high-quality digital solution that fully meets and exceeds all expectations.
Enterprise-grade platform
Easy integration to the existing infrastructure
Enelaitm platform provides pre-built integrations with popular Enterprise software while its versatile architecture allows for almost plug-and-play integration with pre-existing software applications in an Enterprise.
Meeting Enterprise security and data privacy standards
Voiceweb products meet all information security, compliance and payment standards requirements -such as PCI/DSS and GDPR- and have been installed in numerous banks and mobile operators for purchases and financial transactions, after approval from the local Regulators in each country.